FireEye Endpoint Security

Stop the known, find the hidden and fix the breaches that matter
FireEye Endpoint Security
Traditional endpoint security is not effective against modern threats; it was never designed to deal with sophisticated or advanced persistent threat (APT) attacks. To keep endpoints safe, a solution must quickly analyze and respond to such threats.
FireEye Endpoint Security combines the best of legacy security products, enhanced with FireEye technology, expertise and intelligence to defend against today’s cyber attacks. FireEye uses four engines in Endpoint Security to prevent, detect and respond to a threat.
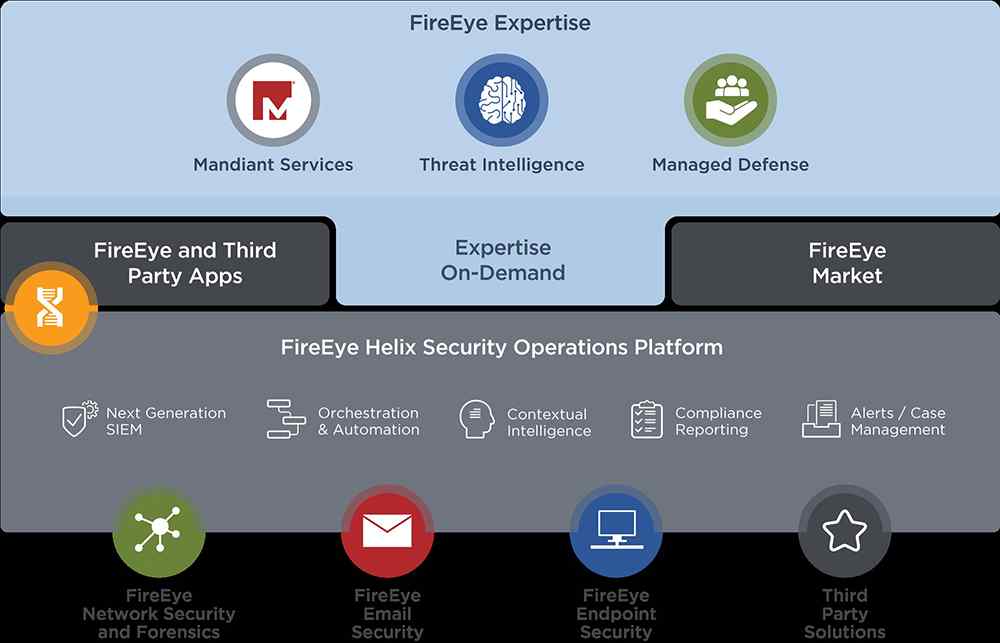
The FireEye services can be used in combination to provide the best possible protection and transparency.
To prevent common Malware, Endpoint Security uses a signature based endpoint protection platform (EPP) engine. To find threats for which a signature does not yet exist, MalwareGuard uses machine learning seeded with knowledge from the front lines of cyber attacks. To deal with advanced threats, endpoint detection and response (EDR) capabilities are enabled through a behavior-based analytics engine. Finally, a real-time indicators of compromise (IOC) engine that relies on current, front line intelligence helps find hidden threats. This defense in depth strategy helps protect vital information stored on customer endpoints.
Datasheet Order NowIKARUS Security Software Sales-Hotline:
Support - +1-650-273-5849 Sales - +1 -574-358-4378
»With FireEye Endpoint Security we have been able to slash the industry average time to detection by almost 98%.”«
Tom Webb
Director of Information Security Operations, University of South Carolina
Even with the best protection, breaches are inevitable. To ensure a substantive response that minimizes business disruption, Endpoint Security provides tools to:
- Search for and investigate known and unknown threats on tens of thousands of endpoints in minutes
- Identify and detail vectors an attack used to infiltrate an endpoint
- Determine whether an attack occurred (and persists) on a specific endpoint and where it spread
- Establish timeline and duration of endpoint compromises and follow the incident
- Clearly identify which endpoints and systems need containment to prevent further compromise
